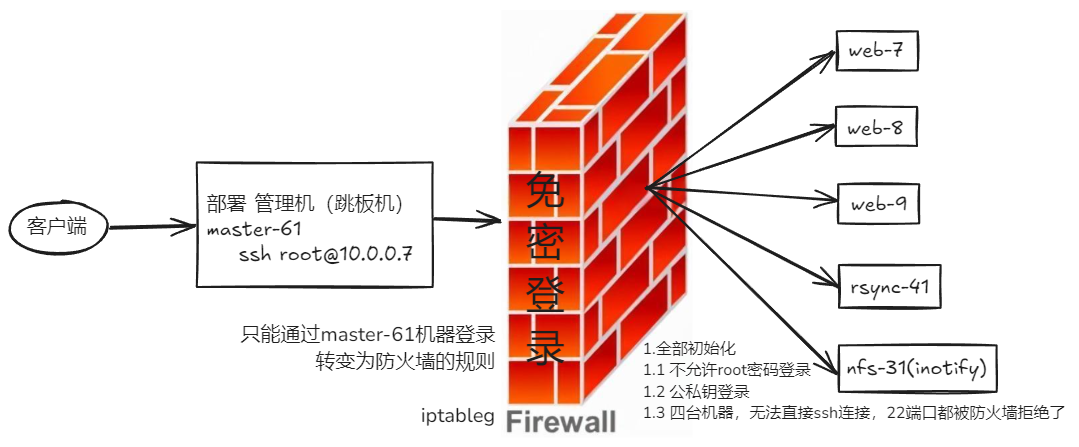
架构图
根据要求完成部署
根据如下要求,完成部署过程
1.恢复7、8、9、31、41所有机器的快照
7 8 9 web服务 nginx
172.16.1.xx
nfs-31 提供共享文件存储
rsync-41 提供数据备份的机器2.在61机器,远程一键脚本化,部署这6台机器
master-61机器远程的,操作目标机器,让它安装好对应的服务
web-7
1.安装软件
2.修改配置文件
3.启动服务
4.挂载nfs
根据服务相关性,需要有先后的部署关系
rsync-41
1.安装软件
2.修改配置文件
3.创建rsync对应的数据目录,配置文件,授权
4.启动服务
nfs-31 + lrsync实时同步
1.安装软件
2.修改配置文件
3.创建nfs相关的数据目录,授权
3.启动服务
4.安装lsync
5.修改lsync配置文件
6.启动服务3.检查整体应用可用性
1.从nginx作为入口,nginx默认的网页根目录
/usr/share/nginx/html 写入数据
2.同步到nfs机器上
3.同步到rsync机器上阶段1:手动部署
master-61建议修改登录别名
alias sshweb7='ssh root@172.16.1.7 -p 22999'
alias sshweb8='ssh root@172.16.1.8 -p 22999'
alias sshweb9='ssh root@172.16.1.9 -p 22999'
alias sshnfs31='ssh root@172.16.1.31 -p 22999'
alias sshrsync41='ssh root@172.16.1.41 -p 22999'
想要永久生效就写入/etc/profile
[root@master-61 ~]#vim /etc/profile
[root@master-61 ~]#source /etc/profile
[root@master-61 ~]#alias
alias sshnfs31='ssh root@172.16.1.31 -p 22999'
alias sshrsync41='ssh root@172.16.1.41 -p 22999'
alias sshweb7='ssh root@172.16.1.7 -p 22999'
alias sshweb8='ssh root@172.16.1.8 -p 22999'
alias sshweb9='ssh root@172.16.1.9 -p 22999'Windows免密登录master-61
1.Windows生成私钥对儿,默认存放在~/.ssh/id_rsa下
#在git-bash命令终端执行
saber@DESKTOP-PLEIBP7 MINGW64 ~/.ssh
$ ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/c/Users/33521/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /c/Users/33521/.ssh/id_rsa
Your public key has been saved in /c/Users/33521/.ssh/id_rsa.pub
The key fingerprint is:
SHA256:zZ55BiKQLf6YZWUMFI3uI11XmilCQt6FNwZ8zLKwSxQ saber@DESKTOP-PLEIBP7
The key's randomart image is:
+---[RSA 3072]----+
| .E+=O. |
| .++*+O . |
| .=*o*+. = |
| .oo+ooo= |
| ..++oSo+ |
| o*+. o + |
| o... + o |
| o |
| |
+----[SHA256]-----+
saber@DESKTOP-PLEIBP7 MINGW64 ~/.ssh
$ ls
id_rsa id_rsa.pub
2.发送Windows的公钥给master-61机器
$ ssh-copy-id root@10.0.0.61
3.查看Windows发送到master-61机器的公钥
[root@master-61 ~]#cat ~/.ssh/authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCvnlydF6Ref9wUtndbto/tPK1rYsPCKohDT1QlMd8DiS1pFHhSylpmO0+/XIQrDLSEnteJLXdhh4QU4DGvLocmijaMvDo1+SsluYV4l1n/iqgkubyntAjL1Dkd22RuyVP35dojTrZowAuplizXQv0ZlkrI+8NI6pQrtUwGS7TgimPIp5nC5GbHymJBm0iFmu+0NPzeVoEDF1l1CijubWgJGy/s+fGbmXY5ESH/rNFGWeykM+DObsUh7/h8w8fELC2e6b8lk6AAOXXX8aI9OkIifT+j5wp26bAk2QgV8swYA3VYGuuiBZw/y4jXA6b6UguzPMvz0mUYTOlSdYSNBlpRRYwybz6ij+SdKkScukj78c5qYe7YAt3fCv+PQgO2y4XmgSQMRhErre02RthiJYNi5+Lqiq2/dJzEOQ4m0Zu9AAPV6J7Pm+AifxuhTfbXW2kJu6K4HRx2pmv9H4tkiT7BaHtRQ0iDRcnoy3d1/B3J4s0n1ZCsAcgS69dm3aqdSYE= saber@DESKTOP-PLEIBP7master-61免密登录web-7、web-8、nfs-31、rsync-41
1.在master-61机器生成公私钥对儿
[root@master-61 ~]#ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
Created directory '/root/.ssh'.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa.
Your public key has been saved in /root/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:J8K8y+N5g9B1mW187j2rjBjb7PtMKj9sJenR7YBs5wU root@master-61
The key's randomart image is:
+---[RSA 2048]----+
| |
| |
| = |
| o . + +E. |
| .+.S.o.+oo |
| . .o o B =.o |
| ... .+ *o+. |
| .ooo.*=*..o.|
| .=o +=O+=..o|
+----[SHA256]-----+
2.检查公私钥
[root@master-61 ~]#ll ~/.ssh/
total 8
-rw------- 1 root root 1675 Sep 15 10:04 id_rsa
-rw-r--r-- 1 root root 396 Sep 15 10:04 id_rsa.pub
[root@master-61 ~]#cat ~/.ssh/id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCgZC+ZaiV40U1eus2XeP5zaMSTfAwjajxTBwijPl/Ld5whyIA+bg8U2j7ctS5hFETrt/45ROgRrAzoq6OaurZDwiVUalvuitwBcjQwidkSkM3P2KBFNmLo4Atg/2eTXfKtMjihG1YWOZEIAQ2WN5U3J+fdFTvwz7Rh16ZDMpZHB1eQJZGy+3zCenhE1pFHpKW+kZymPFS9KuH2k/VGf9AF4xXEm/dCzOXaJrT2XEL4u/lU6JP50AQ/qlJXa4uZ/vVWz5+Hdfwt5//4gZzOILyroc4vfXn7K7uLFsS/HOeKD3iG4S99LDJQmGXXd8Tt/E9Z5Kazr+1G6VwO+90JmB5L root@master-61
3.发送master-61的公钥,给web-7、web-8、web-9、nfs-31
[root@master-61 ~]#ssh-copy-id root@web-7
[root@master-61 ~]#ssh-copy-id root@web-8
[root@master-61 ~]#ssh-copy-id root@web-9
[root@master-61 ~]#ssh-copy-id root@nfs-31
[root@master-61 ~]#ssh-copy-id root@rsync-41
4.查看对应机器有没有接收到master-61发送的公钥
[root@web-7 ~]#cat ~/.ssh/authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCgZC+ZaiV40U1eus2XeP5zaMSTfAwjajxTBwijPl/Ld5whyIA+bg8U2j7ctS5hFETrt/45ROgRrAzoq6OaurZDwiVUalvuitwBcjQwidkSkM3P2KBFNmLo4Atg/2eTXfKtMjihG1YWOZEIAQ2WN5U3J+fdFTvwz7Rh16ZDMpZHB1eQJZGy+3zCenhE1pFHpKW+kZymPFS9KuH2k/VGf9AF4xXEm/dCzOXaJrT2XEL4u/lU6JP50AQ/qlJXa4uZ/vVWz5+Hdfwt5//4gZzOILyroc4vfXn7K7uLFsS/HOeKD3iG4S99LDJQmGXXd8Tt/E9Z5Kazr+1G6VwO+90JmB5L root@master-61
[root@web-8 ~]#cat ~/.ssh/authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCgZC+ZaiV40U1eus2XeP5zaMSTfAwjajxTBwijPl/Ld5whyIA+bg8U2j7ctS5hFETrt/45ROgRrAzoq6OaurZDwiVUalvuitwBcjQwidkSkM3P2KBFNmLo4Atg/2eTXfKtMjihG1YWOZEIAQ2WN5U3J+fdFTvwz7Rh16ZDMpZHB1eQJZGy+3zCenhE1pFHpKW+kZymPFS9KuH2k/VGf9AF4xXEm/dCzOXaJrT2XEL4u/lU6JP50AQ/qlJXa4uZ/vVWz5+Hdfwt5//4gZzOILyroc4vfXn7K7uLFsS/HOeKD3iG4S99LDJQmGXXd8Tt/E9Z5Kazr+1G6VwO+90JmB5L root@master-61
[root@web-9 ~]#cat ~/.ssh/authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCgZC+ZaiV40U1eus2XeP5zaMSTfAwjajxTBwijPl/Ld5whyIA+bg8U2j7ctS5hFETrt/45ROgRrAzoq6OaurZDwiVUalvuitwBcjQwidkSkM3P2KBFNmLo4Atg/2eTXfKtMjihG1YWOZEIAQ2WN5U3J+fdFTvwz7Rh16ZDMpZHB1eQJZGy+3zCenhE1pFHpKW+kZymPFS9KuH2k/VGf9AF4xXEm/dCzOXaJrT2XEL4u/lU6JP50AQ/qlJXa4uZ/vVWz5+Hdfwt5//4gZzOILyroc4vfXn7K7uLFsS/HOeKD3iG4S99LDJQmGXXd8Tt/E9Z5Kazr+1G6VwO+90JmB5L root@master-61
[root@nfs-31 ~]#cat ~/.ssh/authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCgZC+ZaiV40U1eus2XeP5zaMSTfAwjajxTBwijPl/Ld5whyIA+bg8U2j7ctS5hFETrt/45ROgRrAzoq6OaurZDwiVUalvuitwBcjQwidkSkM3P2KBFNmLo4Atg/2eTXfKtMjihG1YWOZEIAQ2WN5U3J+fdFTvwz7Rh16ZDMpZHB1eQJZGy+3zCenhE1pFHpKW+kZymPFS9KuH2k/VGf9AF4xXEm/dCzOXaJrT2XEL4u/lU6JP50AQ/qlJXa4uZ/vVWz5+Hdfwt5//4gZzOILyroc4vfXn7K7uLFsS/HOeKD3iG4S99LDJQmGXXd8Tt/E9Z5Kazr+1G6VwO+90JmB5L root@master-61
[root@rsync-41 ~]#cat ~/.ssh/authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCgZC+ZaiV40U1eus2XeP5zaMSTfAwjajxTBwijPl/Ld5whyIA+bg8U2j7ctS5hFETrt/45ROgRrAzoq6OaurZDwiVUalvuitwBcjQwidkSkM3P2KBFNmLo4Atg/2eTXfKtMjihG1YWOZEIAQ2WN5U3J+fdFTvwz7Rh16ZDMpZHB1eQJZGy+3zCenhE1pFHpKW+kZymPFS9KuH2k/VGf9AF4xXEm/dCzOXaJrT2XEL4u/lU6JP50AQ/qlJXa4uZ/vVWz5+Hdfwt5//4gZzOILyroc4vfXn7K7uLFsS/HOeKD3iG4S99LDJQmGXXd8Tt/E9Z5Kazr+1G6VwO+90JmB5L root@master-61
5.检查是否可以免密登录
[root@master-61 ~]#ssh root@web-7
Last login: Sun Sep 15 10:02:51 2024 from 10.0.0.1
[root@master-61 ~]#ssh root@web-8
Last login: Sun Sep 15 10:02:55 2024 from 10.0.0.1
[root@master-61 ~]#ssh root@web-9
Last login: Sun Sep 15 10:04:35 2024 from 10.0.0.1
[root@master-61 ~]#ssh root@nfs-31
Last login: Sun Sep 15 10:08:59 2024 from 10.0.0.1
[root@master-61 ~]#ssh root@rsync-41
Last login: Sun Sep 15 10:09:10 2024 from 10.0.0.1master-61管理机
1.修改ssh端口为22999
Port 22 改为 Port 22999
2.关闭密码登录
PasswordAuthentication yes 改为 PasswordAuthentication no
3.开启通过公私钥登录
PubkeyAuthentication no 改为 PubkeyAuthentication yes
1. 修改配置文件
[root@master-61 ~]#vim /etc/ssh/sshd_config
1.1 查看该结果
[root@master-61 ~]#grep -Ei '^(pubkey|password|port)' /etc/ssh/sshd_config
Port 22999
PubkeyAuthentication yes
PasswordAuthentication no
2. 重启sshd服务
[root@master-61 ~]#systemctl restart sshd被管理机(web-7、web-8、web-9、nfs-31、rsync-41)
1.修改ssh端口为22999
Port 22 改为 Port 22999
2.关闭密码登录
PasswordAuthentication yes 改为 PasswordAuthentication no
3.开启通过公私钥登录
PubkeyAuthentication no 改为 PubkeyAuthentication yes
1. 修改配置文件
vim /etc/ssh/sshd_config
2. 重启sshd服务
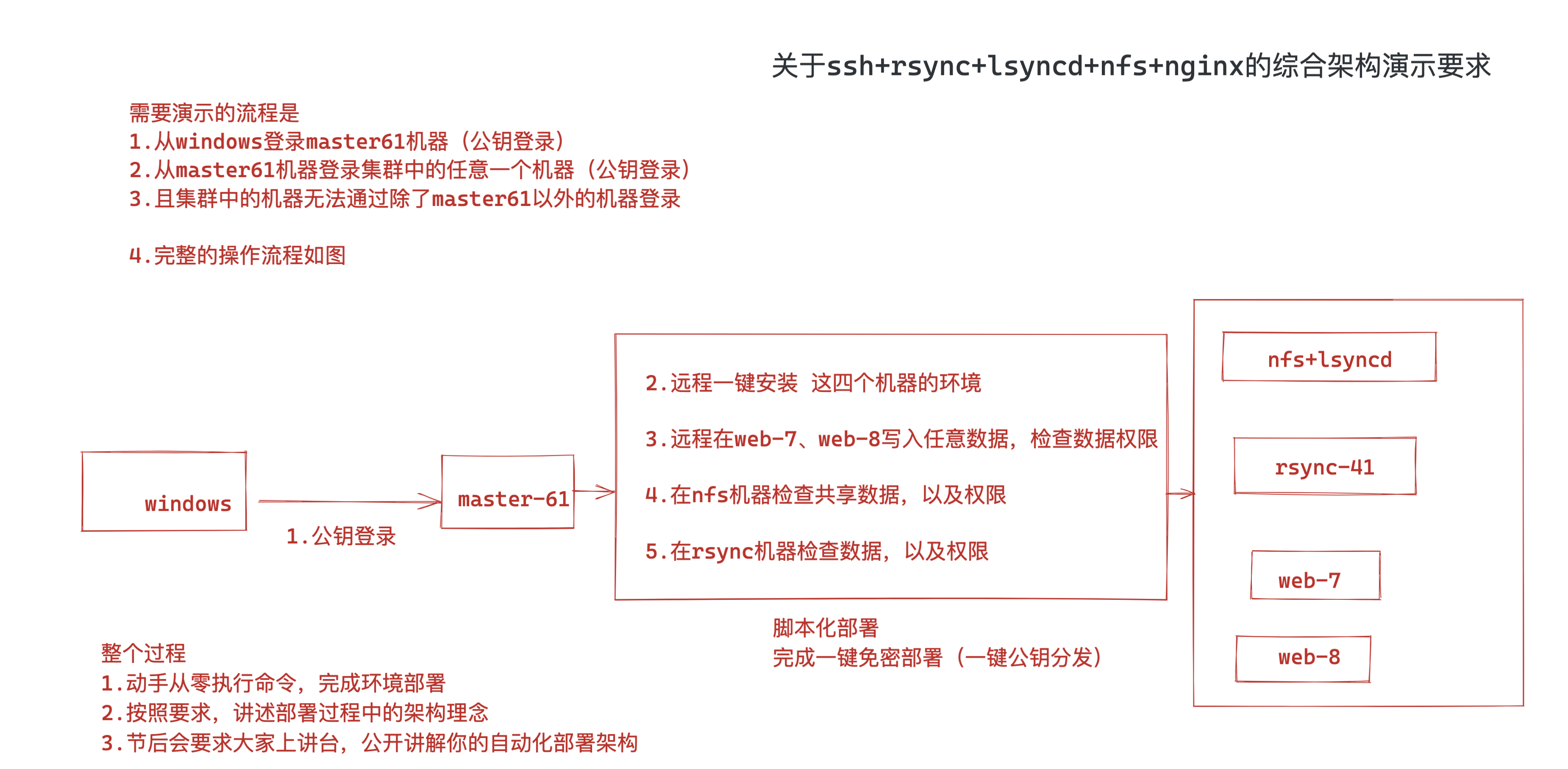
systemctl restart sshd阶段2:编写脚本部署(进阶)
阶段1的ssh环境部署,是手动操作;
现在需要实现脚本一键部署;
1.管理机自动创建公私钥
2.管理机自动分发公钥到备管理机
3.远程修改被管理机的ssh连接端口为22999,监听地址是172.16.1.xx
4.远程修改被管理机不允许密码登录,只能是密钥登录
5.修改完毕后,验证是否生效,远程查看所有被管理主机的主机名批量修改配置文件
友情提醒
客户端机器需要安装
sshpass命令客户端机器是否允许公钥登录
目标机器的sshd配置文件是初始化的
[root@master-61 /scripts]#cat install_ssh.sh#!/bin/bash
#0.安装shhpass
yum install sshpass -y
#1.管理机master-61自动创建公私钥
echo "正在创建公私钥..."
if [ -f /root/.ssh/id_rsa ]
then
echo "密钥对已经存在,请检查!"
else
ssh-keygen -f /root/.ssh/id_rsa -N '' > /tmp/create_ssh.log 2>&1
fi
echo '====================分割线=============================='
#2.管理机master-61自动分发公钥到备管理机
echo "正在分发公钥中...分发的机器列表是{7,8,9,31,41}"
for ip in {7,8,9,31,41}
do
sshpass -p '123123' ssh-copy-id 172.16.1.${ip} -o StrictHostKeyChecking=no > /tmp/create_ssh.log 2>&1
echo "正在验证免密登录结果中...."
echo "远程获取到主机名: $(ssh 172.16.1.${ip} hostname)"
done
echo '====================分割线=============================='
#3.远程修改被管理机的ssh连接端口为22999,监听地址是172.16.1.xx
for ip in {7,8,9,31,41}
do
echo "修改172.16.1.${ip}的ssh端口中..."
ssh root@172.16.1.${ip} "sed -i '/Port 22/c Port 22999' /etc/ssh/sshd_config"
done
echo '====================分割线=============================='
#4.远程修改被管理机不允许密码登录,只能是密钥登录
for ip in {7,8,9,31,41}
do
echo "禁止密码登录参数修改中...当前操作的机器是172.16.1.${ip}"
ssh root@172.16.1.${ip} "sed -i '/^PasswordAuthentication/c PasswordAuthentication no' /etc/ssh/sshd_config"
echo "允许公钥登录参数修改中...当前操作的机器是172.16.1.${ip}"
ssh root@172.16.1.${ip} "sed -i '/PubkeyAuthentication/c PubkeyAuthentication yes' /etc/ssh/sshd_config"
done
echo '====================分割线=============================='
# 5.修改监听内网地址
for ip in {7,8,9,31,41}
do
echo "修改监听地址中...当前操作的机器是172.16.1.${ip}"
ssh root@172.16.1.${ip} "sed -i '/ListenAddress 0.0.0.0/c ListenAddress 172.16.1.${ip}' /etc/ssh/sshd_config"
done
echo '====================分割线=============================='
# 6.批量验证ssh修改情况
for ip in {7,8,9,31,41}
do
echo "当前查看的机器是172.16.1.${ip}"
ssh root@172.16.1.${ip} "grep -E '^(Port|PasswordAuthentication|PubkeyAuthentication|ListenAddress)' /etc/ssh/sshd_config"
done
echo '====================脚本执行完毕=============================='[root@master-61 /scripts]#bash install_ssh.sh
正在创建公私钥...
密钥对已经存在,请检查!
====================分割线==============================
正在分发公钥中...分发的机器列表是{7,8,9,31,41}
正在验证免密登录结果中....
远程获取到主机名: web-7
正在验证免密登录结果中....
远程获取到主机名: web-8
正在验证免密登录结果中....
远程获取到主机名: web-9
正在验证免密登录结果中....
远程获取到主机名: nfs-31
正在验证免密登录结果中....
远程获取到主机名: rsync-41
====================分割线==============================
修改172.16.1.7的ssh端口中...
修改172.16.1.8的ssh端口中...
修改172.16.1.9的ssh端口中...
修改172.16.1.31的ssh端口中...
修改172.16.1.41的ssh端口中...
====================分割线==============================
禁止密码登录参数修改中...当前操作的机器是172.16.1.7
允许公钥登录参数修改中...当前操作的机器是172.16.1.7
禁止密码登录参数修改中...当前操作的机器是172.16.1.8
允许公钥登录参数修改中...当前操作的机器是172.16.1.8
禁止密码登录参数修改中...当前操作的机器是172.16.1.9
允许公钥登录参数修改中...当前操作的机器是172.16.1.9
禁止密码登录参数修改中...当前操作的机器是172.16.1.31
允许公钥登录参数修改中...当前操作的机器是172.16.1.31
禁止密码登录参数修改中...当前操作的机器是172.16.1.41
允许公钥登录参数修改中...当前操作的机器是172.16.1.41
====================分割线==============================
当前查看的机器是172.16.1.7
Port 22999
PubkeyAuthentication yes
PasswordAuthentication no
当前查看的机器是172.16.1.8
Port 22999
PubkeyAuthentication yes
PasswordAuthentication no
当前查看的机器是172.16.1.9
Port 22999
PubkeyAuthentication yes
PasswordAuthentication no
当前查看的机器是172.16.1.31
Port 22999
PubkeyAuthentication yes
PasswordAuthentication no
当前查看的机器是172.16.1.41
Port 22999
PubkeyAuthentication yes
PasswordAuthentication no
====================脚本执行完毕==============================批量重启ssh服务验证结果
1.重启服务,单独拆分为了一个脚本,作用就是重启服务
[root@master-61 /scripts]#cat restart_ssh.sh#!/bin/bash
for ip in {7,8,9,31,41}
do
echo "重启sshd服务中,当前操作的机器是172.16.1.${ip}"
ssh root@172.16.1.${ip} "systemctl restart sshd"
echo "==========================================="
done2.远程查看主机信息
这个脚本,作用就是远程查看主机的配置文件信息
[root@master-61 /scripts]#cat show_hostname.sh #!/bin/bash
for ip in {7,8,9,31,41}
do
echo "远程获取主机名中,当前操作的机器是172.16.1.${ip}"
ssh -p 22999 root@172.16.1.${ip} "hostname"
echo "远程获取主机sshd配置信息,当前操作的机器是172.16.1.${ip}"
ssh -p 22999 root@172.16.1.${ip} "grep -E '^(Port|PasswordAuthentication|PubkeyAuthentication|ListenAddress)' /etc/ssh/sshd_config"
echo "远程查看sshd端口情况,当前操作的机器是172.16.1.${ip}"
ssh -p 22999 root@172.16.1.${ip} "netstat -tunlp|grep sshd|grep -v grep"
echo "========================分割线============================="
done此时还剩下master-61机器未修改了
web-7
web-8
web-9
nfs-31
rsync-41
全部完成了 sshd的配置文件修改,修改了
端口
监听地址
禁止密码登录
允许公钥登录
下一步就是该master-61机器的安全性,
禁止密码登录
允许公钥登录
修改默认22端口
[root@master-61 ~]#grep -Ei '^(pubkey|password|port)' /etc/ssh/sshd_config
Port 22999
PubkeyAuthentication yes
PasswordAuthentication no
[root@master-61 ~]#systemctl restart sshd测试
C:\Users\33521>ssh root@master-61
ssh: Could not resolve hostname master-61: \262\273\326\252\265\300\325\342\321\371\265\304\326\367\273\372\241\243
C:\Users\33521>ssh root@10.0.0.61 -p 22999
Last login: Sun Sep 15 20:30:15 2024 from 10.0.0.1
[root@master-61 ~]#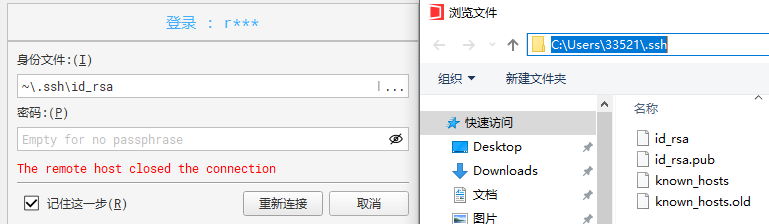
阶段3:远程一键安装综合备份架构
上述的阶段2,一键搭建好了sshd的安全连接环境
只要编写一键安装服务的脚本即可
注意服务的启动顺序
rsync服务部署
rsync-41机器
[root@master-61 /scripts]#cat install_rsync.sh#!/bin/bash
# 1.安装
yum install rsync -y
# 2.配置文件
cat > /etc/rsyncd.conf << 'EOF'
uid = www
gid = www
port = 873
fake super = yes
use chroot = no
max connections = 200
timeout = 600
ignore errors
read only = false
list = false
auth users = rsync_backup
secrets file = /etc/rsync.passwd
log file = /var/log/rsyncd.log
#####################################
[backup]
comment = haloyang.top about rsync
path = /backup
EOF
# 3.创建用户
groupadd www -g 666
useradd www -g 666 -u 666 -M -s /sbin/nologin
# 4.创建目录,授权
mkdir -p /backup
chown -R www.www /backup
# 5.创建密码文件,授权
echo 'rsync_backup:yang666' > /etc/rsync.passwd
chmod 600 /etc/rsync.passwd
# 6.启动服务
systemctl start rsyncd
systemctl enable rsyncd
# 7.检查服务
netstat -tunlp|grep rsync远程拷贝、远程安装
[root@master-61 /scripts]#scp -P 22999 install_rsync.sh root@172.16.1.41:/opt/
[root@master-61 /scripts]#ssh -p 22999 root@172.16.1.41 "bash /opt/install_rsync.sh"
远程检查rsync部署操作
[root@master-61 /scripts]#sshrsync41 "cat /etc/rsync.passwd;ls -ld /backup;id www"
rsync_backup:yang666
drwxr-xr-x 2 www www 6 Sep 15 21:36 /backup
uid=666(www) gid=666(www) groups=666(www)nfs服务部署
nfs-31机器
[root@master-61 /scripts]#cat install_nfs.sh#!/bin/bash
# 0. yum源阿里云yum配置(为了脚本的健壮性,可以配置可靠的yum源)
# 1.安装服务
yum install nfs-utils rpcbind -y
# 2.创建nfs限定的用户、组
groupadd www -g 666
useradd www -g 666 -u 666 -M -s /sbin/nologin
# 3.创建共享目录,修改权限
mkdir /nfs-yang-nginx
chown -R www.www /nfs-yang-nginx
# 4.创建配置文件
cat > /etc/exports <<EOF
/nfs-yang-nginx 172.16.1.0/24(rw,sync,all_squash,anonuid=666,anongid=666)
EOF
# 5.启动服务
systemctl start nfs远程安装
1.远程发送配置文件
[root@master-61 /scripts]#scp -P 22999 install_nfs.sh root@172.16.1.31:/opt/
2.远程执行
[root@master-61 ~]#ssh -p 22999 root@172.16.1.31 "bash /opt/install_nfs.sh"
3.远程检查服务
[root@master-61 /scripts]#sshnfs31 "showmount -e 127.0.0.1"
Export list for 127.0.0.1:
/nfs-yang-nginx 172.16.1.0/24nfs+lsyncd服务
nfs-31机器
[root@master-61 /scripts]#cat install_lsyncd.sh# 1.安装服务
yum install lsyncd -y
# 2.生成配置文件
cat >/etc/lsyncd.conf <<EOF
settings {
logfile ="/var/log/lsyncd/lsyncd.log",
statusFile ="/var/log/lsyncd/lsyncd.status",
inotifyMode = "CloseWrite",
maxProcesses = 8,
}
sync {
default.rsync,
source = "/nfs-yang-nginx",
target = "rsync_backup@172.16.1.41::backup",
delete= true,
exclude = {".*"},
delay=1,
rsync = {
binary = "/usr/bin/rsync",
archive = true,
compress = true,
verbose = true,
password_file="/etc/rsync.passwd",
_extra={"--bwlimit=200"}
}
}
EOF
# 3.创建密码文件
echo "yang666" > /etc/rsync.passwd
chmod 600 /etc/rsync.passwd
# 4.启动
systemctl start lsyncd远程安装lsyncd
1.远程发送配置文件
[root@master-61 /scripts]#scp -P 22999 install_lsyncd.sh root@172.16.1.31:/opt/
2.远程执行
[root@master-61 /scripts]#ssh -p 22999 root@172.16.1.31 "bash /opt/install_lsyncd.sh"
3.远程检查服务
[root@master-61 /scripts]#sshnfs31 "ps -ef|grep lsyncd |grep -v grep"
root 5961 1 0 21:51 ? 00:00:00 /usr/bin/lsyncd -nodaemon /etc/lsyncd.conf测试rsync+nfs
[root@master-61 ~]#ssh -p 22999 root@172.16.1.31 "touch /nfs-yang-nginx/666.png"
[root@master-61 ~]#
[root@master-61 ~]#ssh -p 22999 root@172.16.1.41 "ls /backup"
666.log
666.pngWeb7/8/9机器
[root@master-61 /scripts]#cat install_nginx.sh#!/bin/bash
# 1.安装服务
yum install nginx -y
# 2.创建配置文件
cat >/etc/nginx/nginx.conf <<EOF
worker_processes auto;
error_log /var/log/nginx/error.log;
pid /run/nginx.pid;
# Load dynamic modules. See /usr/share/doc/nginx/README.dynamic.
include /usr/share/nginx/modules/*.conf;
events {
worker_connections 1024;
}
http {
log_format main '$remote_addr - $remote_user [$time_local] "$request" '
'$status $body_bytes_sent "$http_referer" '
'"$http_user_agent" "$http_x_forwarded_for"';
access_log /var/log/nginx/access.log main;
sendfile on;
tcp_nopush on;
tcp_nodelay on;
keepalive_timeout 65;
types_hash_max_size 4096;
include /etc/nginx/mime.types;
default_type application/octet-stream;
server {
listen 81;
server_name localhost;
location / {
root html;
index index.html;
}
}
}
EOF
# 3.启动服务
systemctl start nginx
# 4.挂载目录
yum install nfs-utils -y
mount -t nfs 172.16.1.31:/nfs-yang-nginx /usr/share/nginx/html远程部署
1.远程发送配置文件
[root@master-61 /scripts]#scp -P 22999 install_nginx.sh root@172.16.1.7:/opt
1.1远程批量发送
for web_ip in {7,8,9};do scp -P 22999 install_nginx.sh root@172.16.1.${web_ip}:/opt ;done
2.远程执行
[root@master-61 /scripts]#ssh -p 22999 root@172.16.1.7 "bash /opt/install_nginx.sh"
2.1 远程批量执行
for web_ip in {7,8,9};do ssh -p 22999 root@172.16.1.${web_ip} "bash /opt/install_nginx.sh" ;done
3.远程检查挂载、端口
for web_ip in {7,8,9};do ssh -p 22999 root@172.16.1.${web_ip} "df -h" ;done
for web_ip in {7,8,9};do ssh -p 22999 root@172.16.1.${web_ip} "netstat -tunlp|grep nginx" ;done最终测试
1.在共享存储中,本地创建网页数据文件,提供给所有web机器使用
cat >index.html<<EOF
<meta charset=utf8>
心若在、梦就在。
EOF
2.远程发送给nfs-31机器
[root@master-61 /scripts]#scp -P 22999 index.html root@172.16.1.31:/nfs-yang-nginx/
3.检查rsync-41数据备份情况
ssh -p 22999 root@172.16.1.41 "ls -l /backup"
[root@master-61 /scripts]#ssh -p 22999 root@172.16.1.41 "ls -l /backup"
total 4
-rw-r--r-- 1 www www 45 Sep 15 22:19 index.html
4.检查网站情况
for web in {7,8,9};do curl 172.16.1.${web}:81 ;done
[root@master-61 /scripts]#for web in {7,8,9};do curl 172.16.1.${web}:81 ;done
<meta charset=utf8>
心若在、梦就在。
<meta charset=utf8>
心若在、梦就在。
<meta charset=utf8>
心若在、梦就在。
5. 浏览器访问
http://10.0.0.7:81/
http://10.0.0.8:81/
http://10.0.0.9:81/
6.再次修改页面,查看数据
cat >index.html<<EOF
<meta charset=utf8>
心若在、梦就在。
只不过是从头再来!
EOF
scp -P 22999 index.html root@172.16.1.31:/nfs-yang-nginx/
[root@master-61 ~]#ssh -p 22999 root@172.16.1.41 "cat /backup/index.html"
<meta charset=utf8>
心若在、梦就在。
只不过是从头再来!


